With
Covid19, large numbers of employees are working remotely, not going into the
office, and are rapidly adopting technologies that they hadn’t used before in
order to be able to continue to service their customers.
We at GDPRsimple have always
worked remotely because for part of the year I live in a different state than
my co-founder. This is how we know that there are several key steps that
you need to do immediately to protect your business from regulatory criticism:
- Make a list of the new technological
solutions – known as third party service providers – that you and your entire
team are using. Ideally, steps 2-4 would have been done before you
started using these technologies. However, these recommendations
recognize that the exigencies of getting your business up and running remotely
on short notice may not have allowed for such an orderly process.
Many
organizations now are using far more technologies than they previously used. As
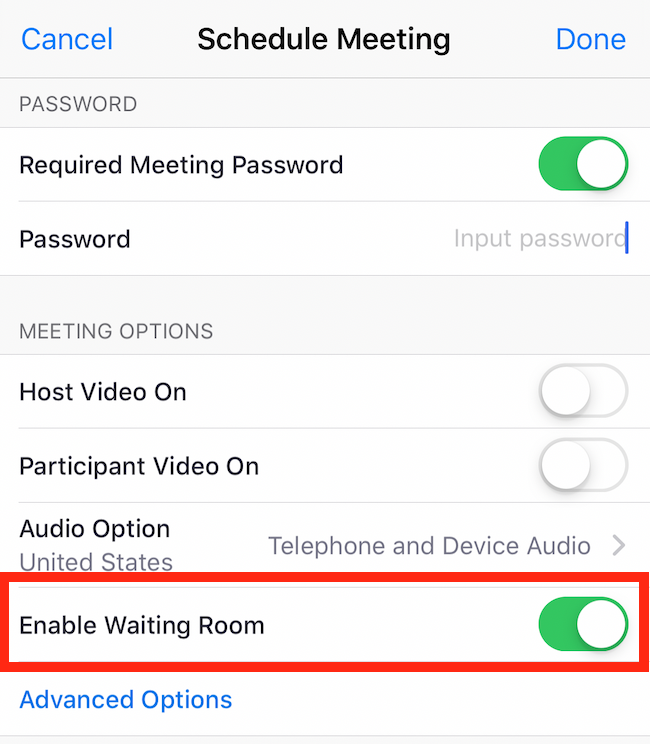
a result of working remotely, many workforces now need to frequently use video
and screensharing. Examples of these technologies are Zoom, Slack and Crowdcast.
Depending on how you use them, each of these technologies may collect
information about you, your employees, and any information you may share about
your users and customers.
- Now take that list and bucket it into
two groups. (There are more groups beyond this such as cloud, but we will
focus on these for now as they relate to the changes in work due to Covid19):
Secure: These are
technologies that are built to be protective of personal data. One of the
value propositions for them has to do with the fact that they securely send,
receive and store information via the Cloud. Examples are DropBox and Box for
file storage and DocuSign for electronic document signing.
Customer
Service: There are
other technologies that are used to help teams to communicate with and about
customers – from segmentation to acquisition to retention and servicing.
These platforms probably have been added to your technological suite as a
result of Covid19 and could be anything from videoconferencing and
screensharing (e.g. Zoom, GoogleHangout, Skype) to
messaging (Slack) to data collection, sorting, and integration (AirTable).
No personal
data should be shared on these platforms. Do not send individual customer
identification numbers or bank account numbers via any of these
platforms. Instead, convey personal information by phone or by a means of
secure transport (e.g. secure email or DropBox or Box).
- Now that you have your two buckets,
look at the privacy policies that these organizations post on their own
websites.
You – as a
leader of your team, department, company – need to know how each of those
companies use, disclose and share personal data collected on their
platforms. In particular, you will want to make sure that the Servicing
Customer platforms do not use, disclose or share the personal data other
than to provide the service you have hired them to provide (e.g. video
conferencing or screen sharing).
- After educating yourself, update your
own privacy policy.
We recommend
you use GDPRsimple to help update
your privacy policy. GDPRsimple contains
logic driven document generators to help you and your company keep these
policies up-to-date. Even more, you can keep a history of the different
versions of the privacy policy, and you can track all of them automatically
within GDPRsimple.
In the
sprint to implement GDPR by May 2018, many organizations fell into the
expedient practice of either using canned privacy policies or copying their
competitor’s privacy policy as their own. These “templates” a) do not
take into account the individual choices of your business, and b) are
out-of-date now because you are using more technology platforms than before
because of Covid19. Indeed, recently the regulator for the UK fined a
pharmacy £275,000 for, among other things, merely copying National Pharmacy
Association policy templates – read more here.
We at GDPRsimple built a
platform for you – the CEO, the team leader, the entrepreneur. The GDPR
is complicated, and we wanted to simplify it for you. Contact us today at info@gdprsimple.com to learn
more.